Is this email SPAM?
First some interesting information regarding the origins of the word. For us who are a little "long in the tooth", we know Spam as a faux meat product from the 70's. It was often referred to as "fake meat" and therefore became synonymous with "fake message". Of course, who could forget the 70's Monty Python Movie where a bunch of actors are singing "SPAM, SPAM, SPAM, SPAM, SPAM".... For more information on the origins of this word, visit:
So what to look for? Spammers often attempt to trick you into clicking on links in an effort to obtain your userid and password. The challenge for end-users is most of us live a very hectic life and often "click" without thinking. Here are some things to look for:
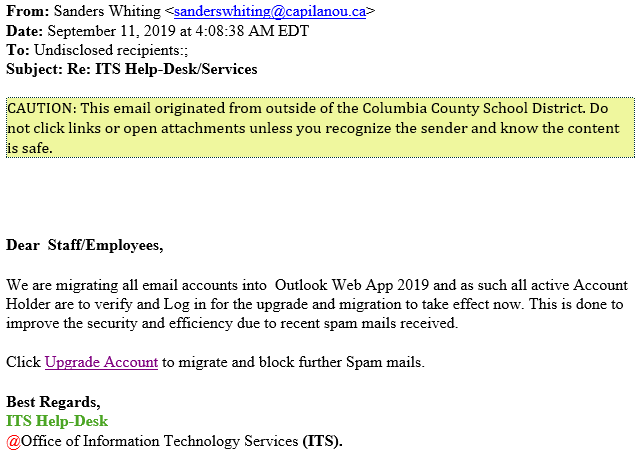
1. Look to see where the email came from. Look at the sender's email address.
Does this look like it is coming from someone you know? Look at the "FROM" address, do you know anyone in Canada (that's the country code for Canada "ca"). This is the first item you should look at. WARNING: If someone you know email has been compromised, they could be sending you SPAM from that account, so don't just go by this.
2. Look at the content of the message. Does it read properly?
Most foreign SPAMMERS do not use proper english? In this case, it's pretty good; however, it just doesn't read right.
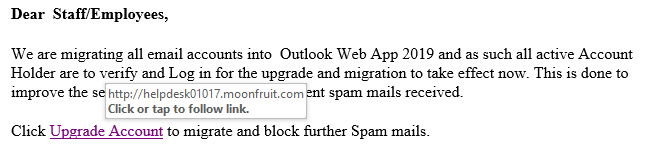
3. If you hover your mouse over the link, you will see where the embedded link is taking you.
In this email, if you were to hover your mouse over the "Upgrade Account" link, you will see that the embedded link (where the link is really set to go to) is displayed. As you can see from the example below, this link is set to take you to a place called "moonfruit.com", which is a Internet website hosting provider (gandi.com) in London, England.
4. Finally, when in doubt, don't click the link
Instincts are something we all have. If you think it's not legitimate, it most likely is not. When in doubt, send your TSS an email asking them to verify the link.
We all have a responsibility to be good Digital Citizens. Working together we can combat spammers and safeguard our students data.